What is Web Application Security?
Malicious attacks, infiltration, breaking firewall norms, and several other malpractices are quite usual these days. Especially, when it comes to online apps, the need for web application security becomes inevitable. The stigma of malicious code practices and cyber-attacks leads to secure web space with consistent testing and implementation of security best practices with the help of web development companies.
So, by now, you would have clearly understood what is the intention of this blog. With the aim to shed maximum light on how much importance this hold to protect your web apps. We will try and cover almost all the aspects of web application security. So, for that, we need to start with understanding Web Application Security.
1. What is Web Application Security?
Web application security is the practice of protecting websites and online web services from various security threats by ignoring unattended errors in the code of the web application. These are also called web application attacks.
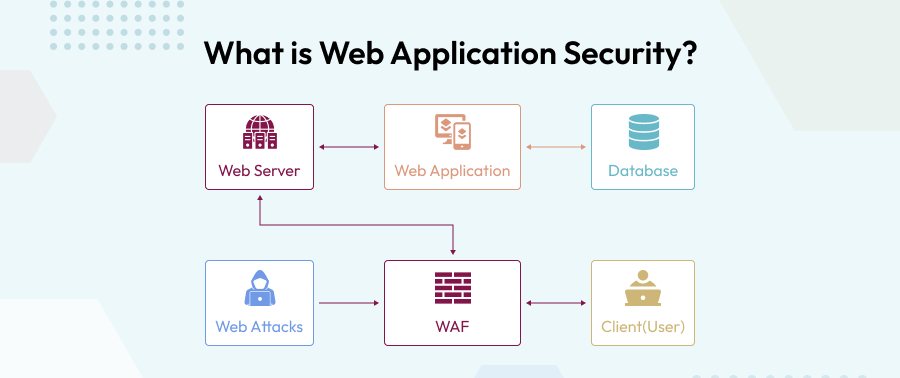
Content management systems, database administration tools, and SaaS applications are some of the easiest targets for online attackers.
Also, if there is some intrinsic complexity in the source code, then you might need to enhance the probability of neglected vulnerabilities and malicious code tampering.
You as a business will need to keep a track of malicious attacks on your web apps. You need to make them high-priority targets for everyday operations. If you ignore this, you will end up paying for something that is unnecessary.
If there is a delay in protecting the information, it will hamper high-value details, such as sensitive personal information obtained through effective source code tampering.
Ease of execution, because most attacks can be readily automated and deployed indiscriminately against thousands, tens, or even hundreds of thousands of targets at once.
So, what can be done to protect your web apps from these unexpected and unpredictable security concerns? As a precautionary step, you can test the web application firewalls before forwarding them to the next step of testing.
2. What is the Importance of Web App Security Testing?
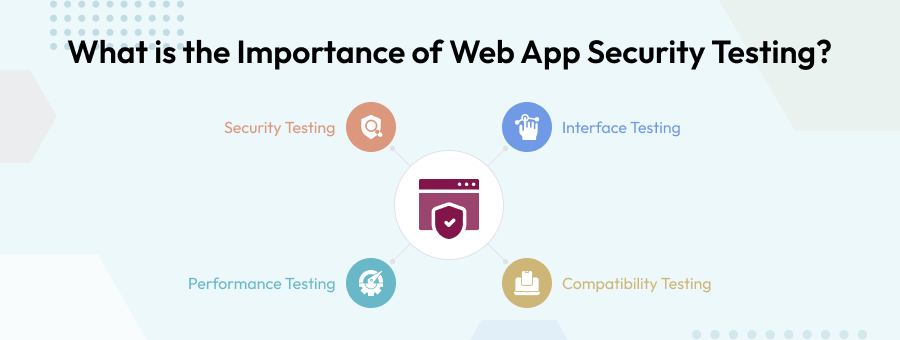
When there is ignorance, hacking or unexpected security vulnerabilities, a need for web security testing arises. The identification of security issues, glitches, or even flaws in web applications and their setup is the end goal of web security testing . There is an application layer which becomes the primary target, because it runs on the HTTP protocol. You can send different input forms to a Web application to understand the problems and make the system respond in the most unexpected ways. It is the most obvious way to test its security. Application layer attacks are so common these days. The results of these tests can be anything which will help us to see if the system is doing anything that is abnormal or functioning as unexpected.
It’s also vital to realize that Web security testing entails more than just verifying the application’s security features such as authentication and transparent communication.
3. Common Web Application Vulnerabilities
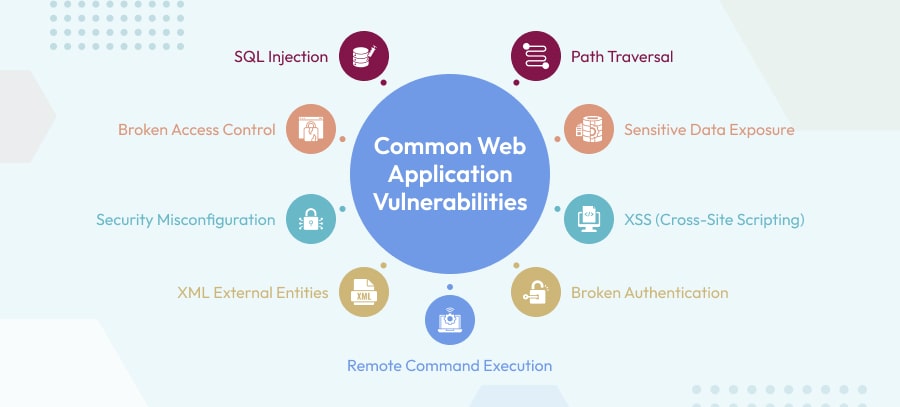
The attacks on web applications are very common but how the attackers happen to attack users is mysterious. Therefore, it is important for companies to understand how these attacks happen and how they can protect it from businesses. Majorly, there are four types of security attacks, we will understand each one in brief.
SQL Injection
When an attacker uses a SQL injection, it means the attacker targets the stored data of vulnerable websites. It can be anything from user passwords or sensitive financial information.This data breach attack, SQL injection attack, involves inserting malicious code into a website or web and mobile based application.
XSS (Cross-Site Scripting)
When hackers run malicious JavaScript on any victim’s browsers, such threats are known as cross-site scripting, or XSS.
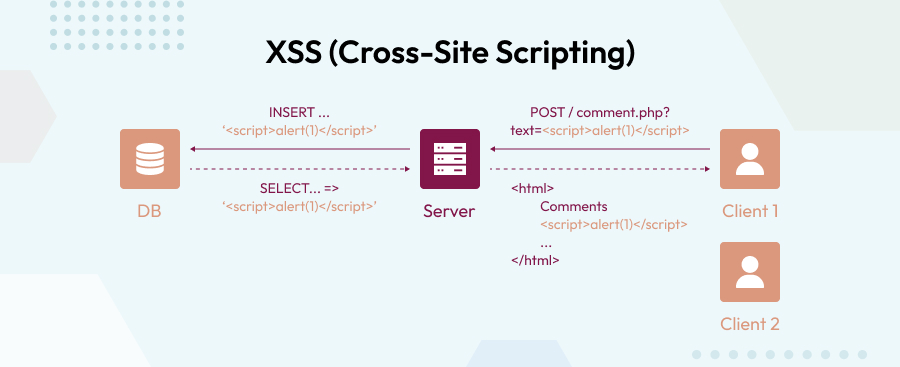
In contrast to Remote Code Execution (RCE) attacks, the code is executed within the browser of the user. Typically, the attacker does not have complete control of the site at the time of injection. Instead, the bad actor places their harmful code on top of a real website, fooling browsers into running their virus every time the site is loaded.
Remote Command Execution

Identifying remote code execution vulnerabilities is a type of software or web app security problem where there is a remote system connected through a LAN, WAN, or the internet that allows malicious aspects to run whatever code they want on a remote system. RCE is part of the wider category of arbitrary code execution (ACE) flaws. However, as there is an immense use of the internet, so is the effect of RCE vulnerabilities rising dramatically.
Path Traversal
An attacker can use a path traversal vulnerability to get access to files on your web server that they shouldn’t have access to. They directly attack the root server. They accomplish this by deceiving the web server or the web application that runs on it into returning files that aren’t in the web root folder.
Broken Authentication
Everyone is aware of the fact that authentication is of utmost importance. This is one of the strongest loopholes in this web application security process. Authentication is a method of verifying a user’s identification by associating incoming data with a set of credentials, such as biometric data, a password, and so on. Broken authentication, on the other hand, indicates that the session management ID or user credentials have been compromised.
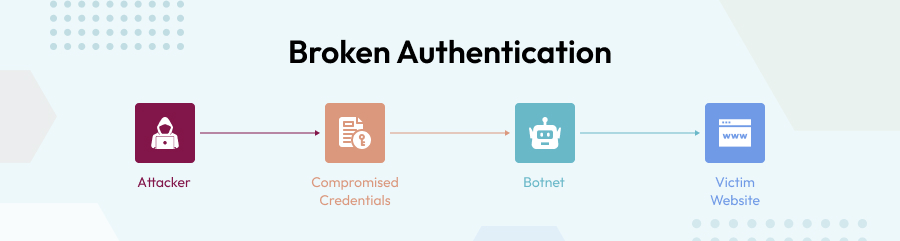
This can also take place because of insufficient user credential protection, weak or predictable passwords and logins, and passing the session ID are all examples of broken authentication.
Sensitive Data Exposure
In this type of data breach, it is quite easy to guess what will happen in this part. Here in the web application security involves the disclosure of confidential information such as phone numbers, account information, credit card details, and so on. Security experts should be aware of the data exposure vulnerability since it may lead to more unfavorable effects such as broken authentication, injection, middle man hampering, and other forms of attacks.
Broken Access Control
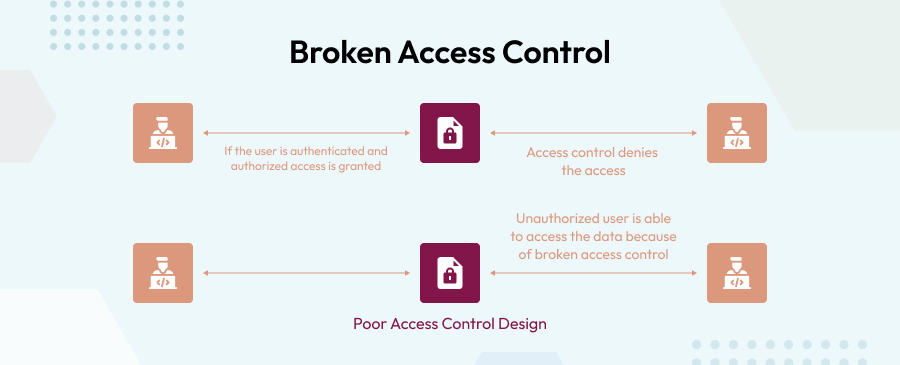
Broken access control is a sort of online application vulnerability in which users are able to perform activities that they should not be able to perform. It may be used by developers to connect other user accounts, edit information inside them, access sensitive data, and, in the worst-case scenario, gain entire control of the web app. The most typical sources of access control vulnerabilities are low-quality functional testing and only manual approach.
XML External Entities
In this type, web applications that parse XML input are targeted by XXE attacks. They frequently occur as a result of outdated or improperly configured XML processors. Hackers can use this vulnerability to gain access to the backend, external systems and perform cross-site request forgery.
Security Misconfiguration
Isn’t security misconfiguration a typical security breach method? It’s an issue caused by security flaws or a lack of security measures. The majority of programmers are insecure because of insufficient settings, long-standing default configurations, unencrypted data, unnecessary operating services, and other considerations. Misconfigured security may lead to unintentional data breaches, ruining a company’s reputation and resulting in significant financial losses.
4. Different Types of Security Tests
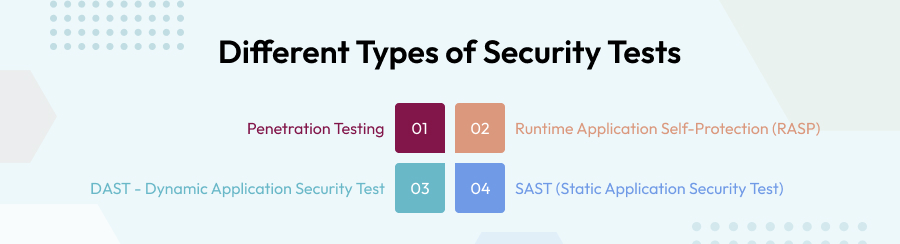
Testing your web application before it goes into the market or in the next phase of software development life cycle can ensure that your app is protected from all the external vulnerabilities. In the market, there are numerous types of testing available which is practiced by your business and can let you save a lot of unnecessary spend on mitigating security flaws. Majorly, we know four ways of security testing
Penetration Testing
In this type of testing there is an application security test performed that is ideal for essential web applications, particularly those that are undergoing significant modifications. By performing this test, you can eliminate significant attack scenarios, and the evaluation uses business logic and adversary-based testing.
Runtime Application Self-Protection (RASP)
In this method, the growing application security needs can incorporate a variety of technical ways to make changes within an application so that the data threats may be watched and hopefully prevented in real time as they occur.
DAST -Dynamic Application Security Test
For apps with minimal risks and critical apps undergoing common upgrades or revisions, combining DAST with some non-automated security testing for common vulnerabilities is the ideal technique. When it is done on a regular basis, there will be no severe issues.
SAST (Static Application Security Test)
This web application security strategy includes both automated and manual testing approaches. It’s ideal for detecting issues without having to run apps in a live environment. It also allows network engineers to scan source code to detect and fix software security flaws in a systematic manner.
5. What are the Best Practices to Mitigate Vulnerabilities?
The only savior for you in this is how you approach day-to-day vulnerabilities. Using up-to-date encryption, demanding adequate authentication, regularly patching or vulnerabilities, and maintaining an excellent and robust software development regime are all important measures in safeguarding web apps against exploitation. There are three ways you can follow;
WAF stands for Web Application Firewall, and it protects against attacks on the application layer. A web application firewall, often known as a WAF, is an automated tool that protects an online application against malicious HTTP traffic. The WAF protects against attacks including cross-site forgery, cross-site scripting, SQL injection, and DDoS mitigation by putting a filtration barrier between the targeted server and the attacker.
DDoS attacks or distributed denial-of-service attacks- It is a typical way to interrupt an online application. DDoS attacks can be mitigated using a number of tactics. This includes eliminating the voluminous traffic from our end and leveraging a secure network to manage trustworthy requests without a hitch.
Another way for this is using DNS Security aka DNSSEC protection
The DNS acts like a phonebook for the Internet and allows web browsers to look up the correct server using IP addresses. There are hijackers who will attempt to interrupt this DNS request process through DNS cache, or on-path attacks and any other methods of interfering. By adding security to this layer, you are securing the address and not allowing any type of malfunctions.
6. Web Application Security Checklist
Several factors might seem fruitful when it comes to security of web apps, but it is important to know which ones will make a difference. Securing web apps may be done in a variety of ways. Here we have prepared a list where if there is any web application that needs to be safeguarded then this is the security checklist to include the following procedures:
Data collection- When you collect data, you must ensure that captured data has no loopholes. For that go over the program and you should look for input data points and client-side codes. Identify and categorize content that is hosted by a third party.
Authorization – Here if you want to find an escape clause, you must look for path traversals. It should be located in all directions- vertical and horizontal access control problems, missing authorization, and direct object references while testing the application.
Data security- Secure all data communications with cryptography. Has any sensitive information been encrypted? Have you employed any algorithms that aren’t up to snuff? Are there any random errors?
Denial of service- Test for anti-automation, account lockout, HTTP protocol DoS, and SQL uncertainties. DoS will improve application’s resilience against denial of service attacks. This will not cover security in contrast to high-volume DoS and DDoS attacks, which require a mix of filtering technologies and scalable resources to resist.
7. Conclusion
In the end of this comprehensive blog, we can conclude that safeguarding your web apps will make or break your entire app development system. It should be a part of the development plan. As we discussed, there are businesses who consider app protection as an important strategy of their business and work towards it beneficially. Security is an irreplaceable factor for businesses and to survive in this market, it is important for them to confront the hackers by not giving them a single opportunity to break your system. Partnering with companies with a knack in web app security will not only help you safeguard your web apps but also improve your focus on other primary needs and ultimately accelerate profitability.
8. FAQs
1. What is Web application security?
Ans: Web application security refers to the practice of ensuring that websites continue to operate normally, even if they are compromised. The idea is to incorporate various security measures into a Web application in order to safeguard its data from hackers and other threats.
2. What are the features of web security?
Ans: To protect your websites from threats, incorporate these features in your web security:
- 2-factor authentication
- Malware scanning
- Blocking and unblocking
- Login attempt limitation
3. What are the two sides of web security?
Ans: web and database server security, and web application security are the two main components of web security.
Building strong customer relationships in the eCommerce business is a challenging task. And managing these relationships with new possibilities and potential consumers is also a...
 May 25, 2022
May 25, 2022 

Comments
Leave a message...